When we hear Agile, most of us think of software development, Scrum boards, and sprint planning meetings. But Agile is more than just a work methodology — it’s a mindset. The same principles that help teams deliver software effectively can also guide us in building better, more balanced lives.
Here’s how the Agile mindset applies outside the workplace:
1. Sprints: Break Big Goals into Small Steps
In software, work is divided into short, manageable sprints. The same approach works beautifully in life.
- Instead of setting overwhelming yearly goals, focus on 1–2 week mini-goals.
- Want to get healthier? Start with a 2-week sprint of daily walks instead of planning a perfect diet and workout plan all at once.
- Want to learn a new skill? Break it into “sprints” like Week 1: Setup tools, Week 2: Basics, Week 3: Projects.
Small, consistent wins add up to big progress.
2. Retrospectives: Reflect, Don’t Judge
After every sprint, Agile teams hold a retrospective to discuss what worked, what didn’t, and what can be improved.
In life, this means pausing regularly to check in with yourself:
- What did I do well this week?
- What drained my energy?
- What can I try differently next week?
This turns failures into feedback and keeps you moving forward without guilt.
3. Adaptability: Embrace Change Gracefully
Agile thrives in uncertain environments where requirements change. Life is no different — plans rarely go exactly as expected.
- Job changes, family needs, or unexpected challenges don’t have to derail us.
- Instead of resisting, adjust your sprint goals and keep moving.
- The key is focusing on what’s within your control and iterating as life unfolds.
Adaptability makes you resilient and future-ready.
4. Continuous Improvement: Growth Over Perfection
Agile emphasizes delivering value early and improving continuously. Perfection is not the goal — progress is.
In personal life, this means:
- Don’t wait for the “perfect” time to start.
- Begin small, learn as you go, and refine along the way.
Life is not about one big release — it’s about constant updates and improvements.
Visual diagram of an “Agile for Life – Personal Sprint Board”
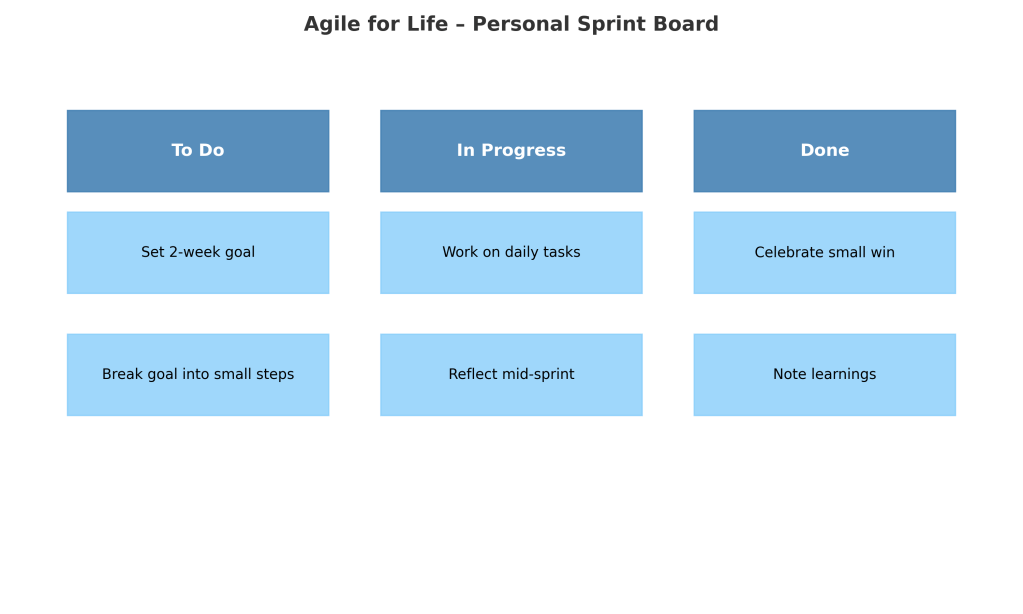
It shows how personal goals can be tracked just like Agile tasks:
- To Do: Set a 2-week goal, break it into steps
- In Progress: Daily tasks, mid-sprint reflection
- Done: Celebrate small wins, note learnings
Key Takeaway
Agile teaches us that progress is more valuable than perfection, learning matters more than failing, and flexibility is stronger than rigidity.
So next time you’re setting goals or facing challenges, try asking yourself:
“How would I handle this if I were running life like an Agile sprint?”
Remember: Live Agile, not just work Agile.